Double click on the download button and follow the instructions to free install and run this iPhone password cracker on your computer. Here we take removing iPhone screen password as an example. Choose the Remove Apple ID feature and connect your iPhone to it with a lightning USB cable. Username: New Huawei. Password: Free Test. How to Crack DC – Unlocker 2? Extract the Content of the.rar “DC – Unlocker 2 Client 1.00.1374” File. Once You Extracted All Compressed Files, Run Main Setup “dc-unlocker2client.exe” File. Disconnect the Internet Connection “Important” and Plug Your USB Modem Device with a. In this case, I will be using the lower case 'l ' as I will only be trying to crack the 'admin' password. After the address of the login form (/dvwa/login.php), the next field is the name of the field that takes the username. In our case, it is 'username,' but on some forms it might be something different, such as 'login.' Access and share logins for savitabhabhi.com. To add a login to this list: register a fake account then share it.
- Kirtu Username And Password Crack Download
- Kirtu Username And Password Crack Free
- Kirtu Username And Password Crack Download
- Username And Password Of Nod32
- Kali Linux Tutorial
- Kali Linux Useful Resources
- Selected Reading
In this chapter, we will learn about the important password cracking tools used in Kali Linux.
Hydra
Hydra is a login cracker that supports many protocols to attack ( Cisco AAA, Cisco auth, Cisco enable, CVS, FTP, HTTP(S)-FORM-GET, HTTP(S)-FORM-POST, HTTP(S)-GET, HTTP(S)-HEAD, HTTP-Proxy, ICQ, IMAP, IRC, LDAP, MS-SQL, MySQL, NNTP, Oracle Listener, Oracle SID, PC-Anywhere, PC-NFS, POP3, PostgreSQL, RDP, Rexec, Rlogin, Rsh, SIP, SMB(NT), SMTP, SMTP Enum, SNMP v1+v2+v3, SOCKS5, SSH (v1 and v2), SSHKEY, Subversion, Teamspeak (TS2), Telnet, VMware-Auth, VNC and XMPP).
To open it, go to Applications → Password Attacks → Online Attacks → hydra.
It will open the terminal console, as shown in the following screenshot.
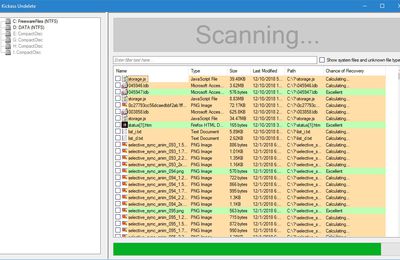
In this case, we will brute force FTP service of metasploitable machine, which has IP 192.168.1.101
We have created in Kali a word list with extension ‘lst’ in the path usrsharewordlistmetasploit.
Kirtu Username And Password Crack Download
The command will be as follows −
where –V is the username and password while trying
As shown in the following screenshot, the username and password are found which are msfadmin:msfadmin
Johnny
Johnny is a GUI for the John the Ripper password cracking tool. Generally, it is used for weak passwords.
To open it, go to Applications → Password Attacks → johnny.
In this case, we will get the password of Kali machine with the following command and a file will be created on the desktop.
Click “Open Passwd File” → OK and all the files will be shown as in the following screenshot.
Click “Start Attack”.
After the attack is complete, click the left panel at “Passwords” and the password will be unshaded.
John
john is a command line version of Johnny GUI. To start it, open the Terminal and type “john”.
In case of unshadowing the password, we need to write the following command −
Rainbowcrack
The RainbowCrack software cracks hashes by rainbow table lookup. Rainbow tables are ordinary files stored on the hard disk. Generally, Rainbow tables are bought online or can be compiled with different tools.
Kirtu Username And Password Crack Free
To open it, go to Applications → Password Attacks → click “rainbowcrack”.
Kirtu Username And Password Crack Download
The command to crack a hash password is −
SQLdict
It is a dictionary attack tool for SQL server and is very easy and basic to be used. To open it, open the terminal and type “sqldict”. It will open the following view.
Under “Target IP Server”, enter the IP of the server holding the SQL. Under “Target Account”, enter the username. Then load the file with the password and click “start” until it finishes.
hash-identifier
It is a tool that is used to identify types of hashes, meaning what they are being used for. For example, if I have a HASH, it can tell me if it is a Linux or windows HASH.
The above screen shows that it can be a MD5 hash and it seems a Domain cached credential.
It’s very easy to forget your password. You've got to contend with lots of passcodes all day long. Losing one's Instagram login key is extremely common.There is absolutely nothing to be anxious about. They will get their password back with utter convenience by using this Gwaa tool.
Username And Password Of Nod32
This could happen that somebody may have accessed your profile and altered your password.The hacking platform can be used to obtain exposure to your profile and to modify a password.
Most people obtain Instagram accounts that are inactive. Because they've not made much use of their profiles,there is also no possibility that they might remember their login details. The hacking tool can be of use in this respect.
The greatest and perhaps most fascinating usage of the login hacking platform on Instagram is that you may play a trick on your colleagues.Instagram is great and it's greater to access your friends’ Instagram accounts.
It could even be employed to catch up with people who break into personal social media profiles by using immoral methods.

The hacking strategy can be beneficial for law enforcement agencies to check up on suspects.Terrorists are also experts at using various social media platforms.